Today, I finally looked at Wapiti, which is a web application vulnerability scanner. It operates on a black box basis (i.e. it doesn’t see the underlying PHP/ASP/Java source code), and effectively tries to ‘break’ any forms on a page.
In order to get it to do anything useful, you’ll probably need to provide it with a cookie file to use. Unfortunately, I couldn’t originally get the provided ‘getcookie.py’ file to work, as the application in question just posted the login form details to ” (i.e. <form action=” method=’post’>)…. after a bit of hacking I fixed this, but it took some time.
Installation is relatively easy – download the .zip file, extract it and change directory into it (e.g. cd wapiti-2.0.X)
Anyway, given we have “webapp” installed at http://orange/webapp, and we wish to test it, we might do something like the following :
- cd src/net
- python getcookie.py ~/cookie.txt http://orange/webapp/login.php
- Enter username/password etc as required to complete the login form
- Script exists, check the contents of ~/cookie.txt – it will look something like :
#LWP-Cookies-2.0
Set-Cookie3: PHPSESSID=3d20841af5de43c718732d80e5d78fe3; path=”/”; domain=”orange”; path_spec; expires=”2010-01-04 22:42:47Z”; version=0
Now we can use wapiti to test any urls ‘behind’ the login screen (as it were) :
wapiti http://orange/webapp/search.php –cookie ~/cookie.txt -v 2 -o ~/report -x http://orange/webapp/logout.php
(We need to exclude the logout page, else our session will get destroyed when wapiti spiders that page…)
Depending on how good the application is, you may see output like :
Found permament XSS in http://orange/webapp/search.php
attacked by http://orange/webapp/search.php?area=on&client_id=on&county=on with fields county=crzbl79tqr&status=x57cjl7m14&website=vk59qqbgmp&name=<script>alert(’11byq04xd1′)</script>&client_id=on®ion=on
and similar for the other vulnerabilities.
If I point my web browser at file:///home/david/report I’ll see a nice HTML report listing the vulnerabilites and so on – similar to the below…
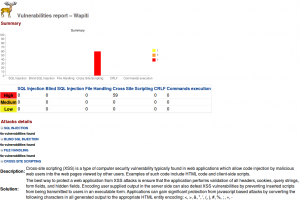
Wapiti appears to detect:
- SQL Injection holes
- Cross Site Scripting (XSS) holes
- File inclusion (local/remote)
- Command execution vulnerabilities
- and others
I’m a bit annoyed I’ve only found this tool now – but also glad I’ve finally found it. I’ve been looking for something that can pick up XSS holes for ages (SQL Injection stuff I could already test using SQLMap, and ensuring I only ever used prepared statements).
Update (July 2011) – cookie file format has changed to xml –
<?xml version="1.0" encoding="UTF-8"?>
<cookies>
<domain name="uk">
<domain name="co">
<domain name="palepurple">
<domain name="david">
<cookie name="PHPSESSID" path="/" value="vmabdv5giph334aq33vb0add67" version="0"/>
<cookie name="globdisc" path="/" value="yes" version="0"/>
</domain>
</domain>
</domain>
</domain>
</cookies>
thanks for the innteresting article, we had use a similar tools SaaS online web application vulnerabilities scanr from GamaSec http://www.gamasec.com
GamaSec identifies application vulnerabilities ( e.g. Cross Site Scripting (XSS), SQL injection, Code Inclusion etc.. ) as well as site exposure risk, ranks threat priority, produces highly graphical, intuitive HTML reports, and indicates site security posture by vulnerabilities and threat exposure.
We were very satisfy with the report and the technical part of the report providing clear recommendation to closed the finding vulnerabilities also the price of the annual servie and the on demand scan schedular was a good add value to the service of http://www.gamasec.com
D
Hello !
A new version of Wapiti (2.2.0) is available since yesterday.
Several new attack modules were added (must be activated with the -m option)
The format of the cookies file has changed – it’s now a nested xml file… which is being awkward about being posted in here…
Hi David,
Great introductory article 🙂
Been looking at wapiti (thanks to your site) for a little while and managed to get it to output results in most cases but sometimed I just get Timeouts on the pages. I looked at using the -n parameter to see if this would help but without success. Is there any chance you could post some examples of using the various parameters that wapiti supports?
Thanks,
Dave
Thanks for a good tutorial david 🙂
when i ran wapiti over url:http://192.168.3.245:7070/lpms.cdac.in/main.do?service=dashboard
after login
success msg is given “A report has been generated in the file generated_report
Open generated_report/index.html with a browser to see this report” but no report is generated in html format only blank template is shown ,
You need to locate the ‘generated_report’ folder – this will be somewhere within the Wapiti source tree. Copy/move/link it to somewhere Apache can find it.
Hey David,
What syntax should be used to scan ONLY for XSS vulnerability, let’s say at abc.com/search= ?
Hi,
Can we use Wapiti from a windows system, mine is windows 8
Yes – I would expect so. You’d need Python installing which shouldn’t be a problem.
How to give command to get cookies for wapiti 2.3.0 version and python 2.7.11 using Ubuntu 14.04
I am not able to use wapiti-getcookie/wapiti-cookie command, NOt sure what will be the exact command to execute for this. Say example- wapiti ???? PLEASE PROVIDE ME details step by step WITH EXAMPLE
Hello David,
We interviewed the developer of Wapiti Web Vulnerability Scanner – thought you’d be interested to read their comments which can be found in this URL:
https://www.concise-courses.com/interview-with-wapiti-developer/
Hello!
We have a web application. We configured OWASP CSRF mechanism in this application. We are performing vulnerability scanning using wapiti but facing one issue. We execute following commands
wapiti-getcookie D:\Wapiti\cookies.json http://<>/<>/jsp/Login.jsp
wapiti.exe http://<>/<> -c D:\Wapiti\cookies.json -b domain -o D:\Wapiti\Scanning_Result -x http://<>/<>/jsp/Logout.do?useraction=logout
After this, instead of all urls from the application, command scans only Login page url, generates report and halts. What options do I need to use so that it will scan all the urls from the application?
thanks